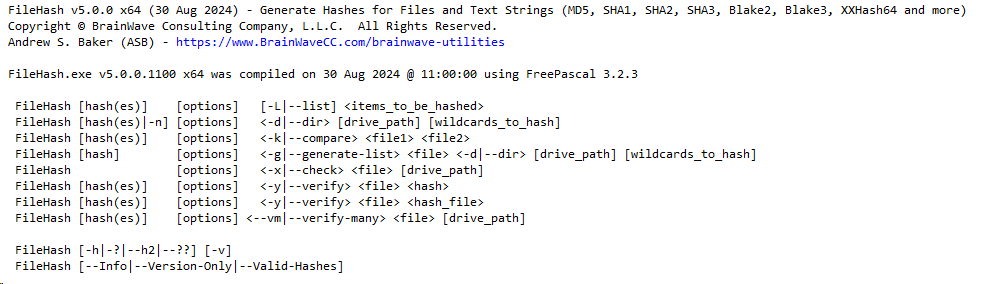
FileHash v5.0 has just been released, and it comes with a focus on making it easier to automate the following two things:
- Obtain the checksums of a set of files in a directory (and subdirectory), and then use that checksum list to compare the same directory structure on the same machine or other machines.
- Verify the checksums of files you download from various websites, either on a one to one basis, or a one to many basis.
A couple of these features (-g and -x, in particular) have been requested by different users for a while, and I was finally able to pursue their implementation.
Let’s take some time here to review a few of those intended use cases, and see how the many available FileHash options come into play. Remember, while FileHash can absolutely be used on a one-off, ad hoc basis, the real reason I developed it was to facilitate automation that I needed to accomplish.
In support of the examples that will follow, consider the following values and their purpose:
| C:\Windows\System32 | This will be our source for a checksum validation file |
| C:\Data | Where we are storing our checksum validation files |
| C:\Data\B-Files.TXT | List of checksums for “C:\Windows\System32\B*.exe” |
| C:\Data\VendorList.TXT | The vendor’s checksum file for all their ISOs |
| C:\Data\MyList.TXT | My test checksum file to test -y and –vm |
| C:\ISOs\MyNewFile.iso | The new ISO files I need to validate before I can install it. |
| “C:\My Downloads” C:\Downloads D:\Binaries | Some of the places where I want to compare the hashes to see how they match with my source files |
Quick validation of a folder tree (-G and -X)
Use the following command to generate the checksum for a directory tree. Include -r to recurse the directory tree. We’re going to keep track of the checksums of a few files in the Windows directory.
FileHash [hash] -g <checksum_save_file> [-r] -d [source_dir] [file_wildcards]
- FileHash -g C:\Data\B-Files.TXT -d C:\Windows\System32 B*.exe
- FileHash -g C:\Data\B-Files.TXT -r -d C:\Windows\System32 B*.exe
To check the same directory later on to see if the files have changed, use the following commands. If no directory is provided, then the current directory is evaluated.
FileHash [–sm] -x <checksum_validation_file> [directory_to_check]
- FileHash -x C:\Data\B-Files.TXT
- FileHash -x C:\Data\B-Files.TXT C:\Windows\System32
- FileHash -x C:\Data\B-Files.TXT D:\Some\Other\Folder
- FileHash -x C:\Data\B-Files.TXT \\ThatServer\ThatShare\ThatFolder
If there are any error messages, they will be reported after the list of files is shown. To include the count of checksums that match in the report, add the –sm parameter.
FileHash [–sm] -x <checksum_validation_file> [directory_to_check]
- FileHash –sm -x C:\Data\B-Files.TXT “C:\Windows\System32”
The -x parameter does not support the selection of a hashing algorithm, because that is provided by -g and stored in the checksum validation file itself. If there are any error messages, they will be reported after the list of files is shown.
If you run -x without supplying a directory, it will use the current directory. If you supply a directory, that is what will be used to search for the files via relative path.
If everything matches, you’ll end up with OK listed for each entry, and the exitcode of the utility will be 0.
If there are any errors, such as a file being changed, or a file not found, or a file being locked or otherwise unable to be hashed, then that combination of errors will return an exitcode between 1 and 7.
Validate a single file via a single checksum (-Y)
If you have downloaded a file (MyNewFile.iso), and want to be sure that it matches the checksum value provided by the vendor / site operator, then you can use the following command, provided that you have the hash as a text value:
FileHash [hash(es)] -y <file_to_validate> [checksum_to_compare_against]
- FileHash -y C:\ISOs\MyNewFile.iso 5a95ba27d0f644a8b78de7fdac849131fab536b8ad4d8a581974d9b77a1ab7f0
You do not have to know if the hash provided is SHA512, SHA256 or something else. FileHash will generate a checksum for each encryption algorithm and compare it to what you have provided. If one matches, you will be informed, and the exitcode will be 0. If there is no match, you will also be informed, and the exitcode will be 119.
For large files (>1GB), you may want to constrain what algorithms are evaluated, as this will save you more than a few seconds vs evaluating them all.
- FileHash –SHA256 –SHA512 -y C:\Downloads\MyNewFile.iso 5a95ba27d0f644a8b78de7fdac849131fab536b8ad4d8a581974d9b77a1ab7f0
Validate a single file via a list of checksums (-Y)
If you have downloaded a file (MyNewFile.iso), and instead of a single checksum value, you are given another file containing multiple checksums, you can use this variation of the command to validate the file against the file containing the list of checksums:
FileHash [hash(es)] -y <file_to_validate> [checksum_validation_file]
- FileHash -y C:\ISOs\MyNewFile.iso “C:\Data\VendorList.TXT”
As with the single checksum, you do not have to know if the hash provided is SHA512, SHA256 or something else. FileHash will generate one for each encryption algorithm and compare it to each checksum entry in the file you have provided. If one matches, you will be informed accordingly, and the exitcode will be 0. If there is no match, you will receive an error message and the exitcode will be 119.
Again, for large files (>1GB), you may want to constrain what algorithms are used, as this will save you more than a few seconds vs evaluating them all, because multiple checksums will be involved.
- FileHash –SHA256 –SHA512 -y C:\ISOs\MyNewFile.iso “C:\Data\VendorList.TXT”
Each line in the checksum validation file can only contain a single checksum, and it must be in the first (left-most) column. If there is anything that follows the checksum, such as a filename, this other data must be separated from the checksum by at least one space and/or one asterisk.
Validate multiple files against a list of checksums (–VM)
This command is very similar to the -x command, except that it does not have the option of reading which algorithm was used to create the validation file. And it is typically confined to a single directory – no subdirectories are supported with this parameter.
The most common use case is that you downloaded some quantity of files from a website, and you want to validate all of them against a list of checksums + files that the site also provided you with — at one time, rather than as a series of separate calls that would be needed with -y. In this scenario, the checksum validation file should contain one hash + one filename per line, separated by at least one space and/or asterisk. No directory name should be included.
Here is the command to read that file and determine if any matches are found. If there is a match, you will also be informed what the algorithm was, and for which file. The exitcode will be 0 if any matches are found, or 1, if not matches are found. Unlike with -x, –vm does not care about any files in the list whose stored checksum no longer matches the calculated checksum. The goal with this parameter is simply to find a name and checksum combo in the file, that matches the same in the selected directory.
FileHash –vm <checksum_validation_file> [directory_to_check]
- FileHash –vm “C:\Data\VendorList.TXT”
- FileHash –vm “C:\Data\VendorList.TXT” C:\Downloads
- FileHash –vm “C:\Data\VendorList.TXT” D:\Binaries
The following command will produce files that can be read by both –vm and –y.
FileHash [hash] -i -o <checksum_save_file> -d [source_directory] [file_wildcards]
- FileHash –Blake3 -i -o “C:\Data\MyList.TXT” -d “C:\My Downloads”
If you have other use cases that you’d like to obtain support for, or you are using FileHash for functions I never imagined, don’t hesitate to reach out and share.
If you find bugs or other issues, please reach out as well.
Happy automation…



